Authentication
To enable Imply Hybrid (formerly Imply Cloud) Auth for your organization, contact your Imply account representative.
Imply Hybrid Auth provides secure authentication to Imply Hybrid through its built-in authentication service. You can enable one or more of the available built-in password policies or set up a new policy for your FreeOTP or Google Authenticator One-Time Password generator to validate one-time passwords.
This article describes how to use Imply Hybrid Auth to facilitate secure authentication to Imply.
Password policies
By default, new organizations do not have password policies associated with them. You can enable and customize password policies for users as required by the security policies of your organization.
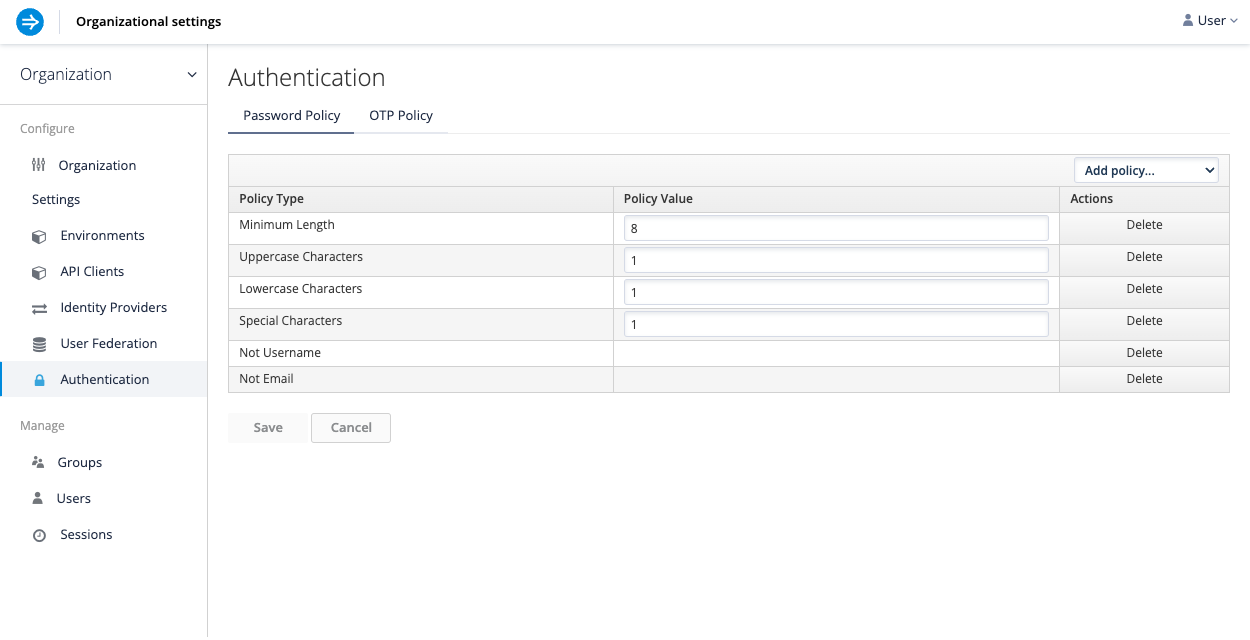
To enable a password policy for your organization, follow these steps:
- In the User management console, select Authentication.
- Click the Password Policy tab.
- Click Add policy to expand the list and select a policy type. For example, you can configure a policy with the following requirements:
- Must be at least eight characters in length
- Must have at least one uppercase character
- Must have at least one lowercase character
- Must have at least one special character
- Cannot be a username
- Cannot be an email
- When finished, click Save.
The following screen capture shows an example password policy:
This applies the settings throughout the organization. To configure policy settings at the user level, select the user first and then make the changes.
Password reset
To allow users to reset forgotten passwords, select Organization Settings from the left menu of the User management console. On the Login tab, toggle the Forgot password switch. This shows a link on the login page for users to click on if they have forgotten their credentials.
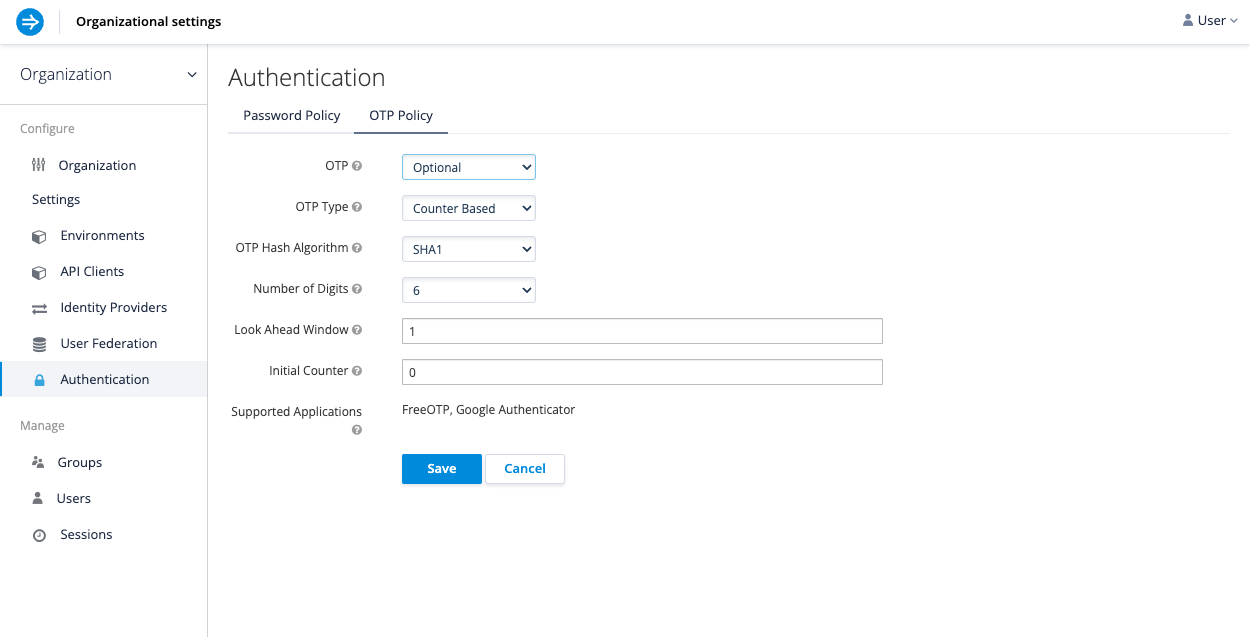
Multi-factor authentication with one-time passwords
Multi-factor authentication (MFA) can significantly enhance user access security. Imply Hybrid Auth works with Google Authenticator and FreeOTP authenticator applications.
Imply Hybrid Auth has a number of policies you can set up for your FreeOTP or Google Authenticator One-Time Password (OTP) generator. There are two different algorithms to choose from: Time Based (TOTP) and Counter Based (HOTP). Each algorithm comes with a set of configuration options.
To enable MFA with an OTP policy, follow these steps:
- In the User management console, select Authentication.
- Go to the OTP Policy tab.
- For the OTP Type, choose counter-based tokens or time-limited tokens.
- Configure other settings based on your requirements, including the OTP hash algorithm, length of the token, and the look-ahead window, which sets a leniency period in case of a synchronization discrepancy between the token generator and server.
The configuration options are as follows:- OTP: Require, disable, or optionally show an OTP if a user has configured that setting in their account.
- OTP Type: The type of the OTP.
- OTP Hash Algorithm: The hashing algorithm used to generate the OTP.
- Number of Digits: The number of digits in the OTP.
- Look Ahead Window: The number of intervals or characters the server should look ahead.
- OTP Token Period (TOTP only): The number of seconds an OTP token should be valid for.
- Initial Counter (HOTP only): The value of the initial counter.
- Supported Applications: Applications that support the current OTP policy.
- Click Save to apply the configuration.
The following screen capture shows an example OTP policy: