Transform Windows event logs
Windows event logs are a feature of Microsoft Windows that capture events for the operating system and applications that run on it. You can use any of the supported ingestion integrations to send Windows event logs to Lumi.
Imply Lumi includes a predefined pipeline to extract fields from incoming Windows events including computer name, error code, and event code as Lumi user attributes. Additionally, Lumi preserves metadata from the forwarder.
This topic describes the Windows log processing pipeline that transforms Windows event logs into Lumi events. For an end-to-end example of using Windows event logs with Lumi, see How to send Windows event logs with S3 routing.
Windows log pipeline
The Windows log pipeline transforms Windows events into Lumi events. The Lumi Windows event parser handles several types of Windows event logs which may have different attributes depending on their origin and purpose.
The default conditions for the pipeline include a filter for sourcetype=*, which includes all events with a sourcetype attribute.
You can add conditions to filter events for the pipeline as needed.
For example, the tutorial limits the events to a single index.
Lumi preserves the original log in the event message.
The following diagram shows a sample Windows event log from the universal forwarder and how its fields appear in Lumi after passing through the Windows log pipeline:
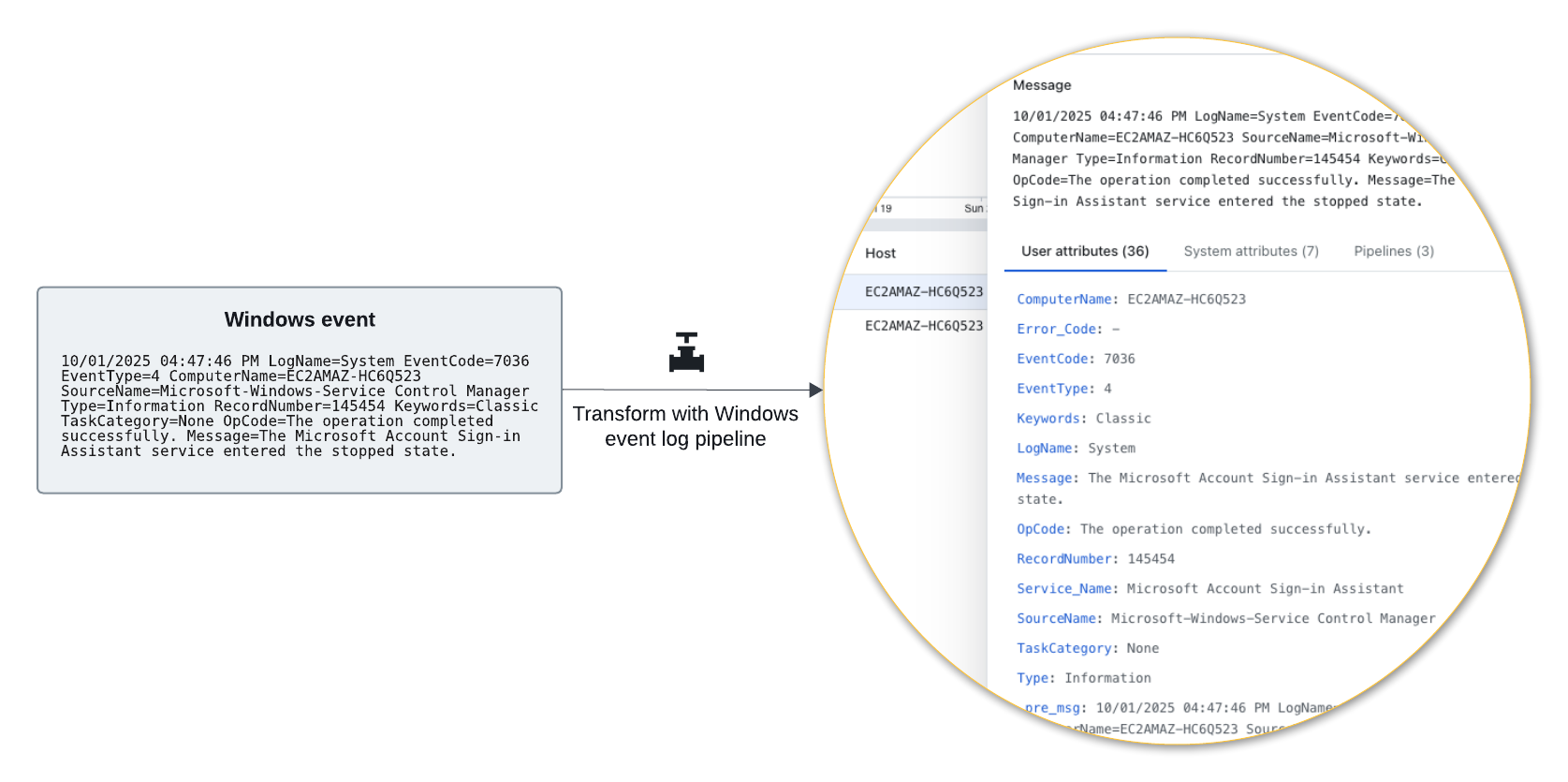
View an example system event log transformed by the Windows log pipeline
{
"message": "10/01/2025 04:47:46 PM LogName=System EventCode=7036 EventType=4 ComputerName=EC2AMAZ-EXAMPLE SourceName=Microsoft-Windows-Service Control Manager Type=Information RecordNumber=145454 Keywords=Classic TaskCategory=None OpCode=The operation completed successfully. Message=The Microsoft Account Sign-in Assistant service entered the stopped state.",
"ComputerName": "EC2AMAZ-EXAMPLE",
"Error_Code": null,
"EventCode": 7036,
"EventType": 4,
"Keywords": "Classic",
"LogName": "System",
"Message": "The Microsoft Account Sign-in Assistant service entered the stopped state.",
"OpCode": "The operation completed successfully.",
"RecordNumber": 145454,
"Service_Name": "Microsoft Account Sign-in Assistant",
"SourceName": "Microsoft-Windows-Service Control Manager",
"TaskCategory": "None",
"Type": "Information",
"_cooked": "_cooked",
"_path": "C:\\Program Files\\MyApplication\\bin\\myapp.exe",
"_pre_msg": "10/01/2025 04:47:46 PM LogName=System EventCode=7036 EventType=4 ComputerName=EC2AMAZ-EXAMPLE SourceName=Microsoft-Windows-Service Control Manager Type=Information RecordNumber=145454 Keywords=Classic TaskCategory=None OpCode=The operation completed successfully.",
"_savedHost": "host::10.103.103.144",
"_savedPort": 9998,
"_sourcetype": "WinEventLog:System",
"body": "The Microsoft Account Sign-in Assistant service entered the stopped state.",
"category": "None",
"dest": "EC2AMAZ-EXAMPLE",
"dvc": "EC2AMAZ-EXAMPLE",
"dvc_nt_host": "EC2AMAZ-EXAMPLE",
"event_id": 145454,
"hf_proxy": "meta_test",
"host": "EC2AMAZ-EXAMPLE",
"id": 145454,
"index": "wineventlog",
"package": 7036,
"product": "Windows",
"remoteport": 51391,
"service": "Microsoft Account Sign-in Assistant",
"service_name": "Microsoft Account Sign-in Assistant",
"severity_id": 4,
"signature_id": 7036,
"source": "WinEventLog:System",
"sourcetype": "WinEventLog",
"status": "stopped",
"vendor": "Microsoft",
"vendor_product": "Microsoft Windows"
}
Use a Windows log pipeline
To use a Windows log pipeline:
-
Add a predefined pipeline and select the Windows log processing pipeline.
-
The pipeline is ready to use without customization if it meets your requirements. If you want to customize the processors, duplicate the pipeline and modify the copy.
-
Edit the pipeline details as required. Make sure the filter expression in the pipeline conditions matches your setup.
-
Reorder the list of pipelines so your Windows log pipeline is in the correct position, and ensure it's enabled.
-
Send Windows event logs to Lumi using your chosen ingestion integration.
-
Check the Lumi integration to preview incoming data. In this example an S3 ingest action added the logs:
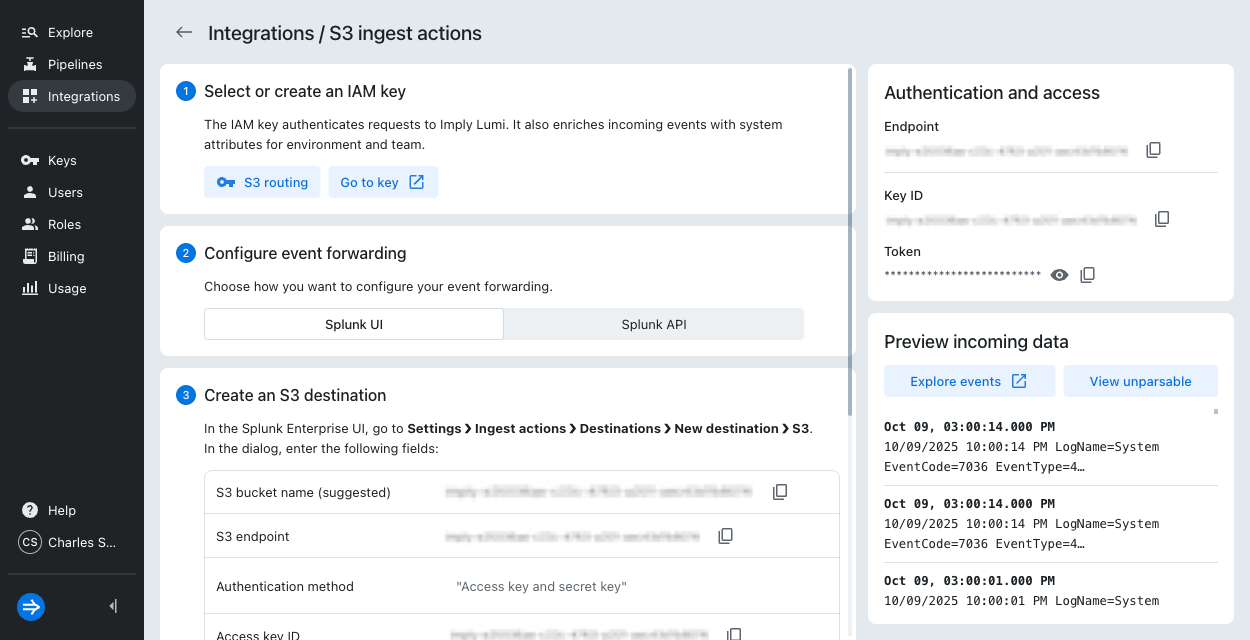
-
Query Lumi to see the enriched Windows log events. The event details pane shows the pipeline that processed the event:
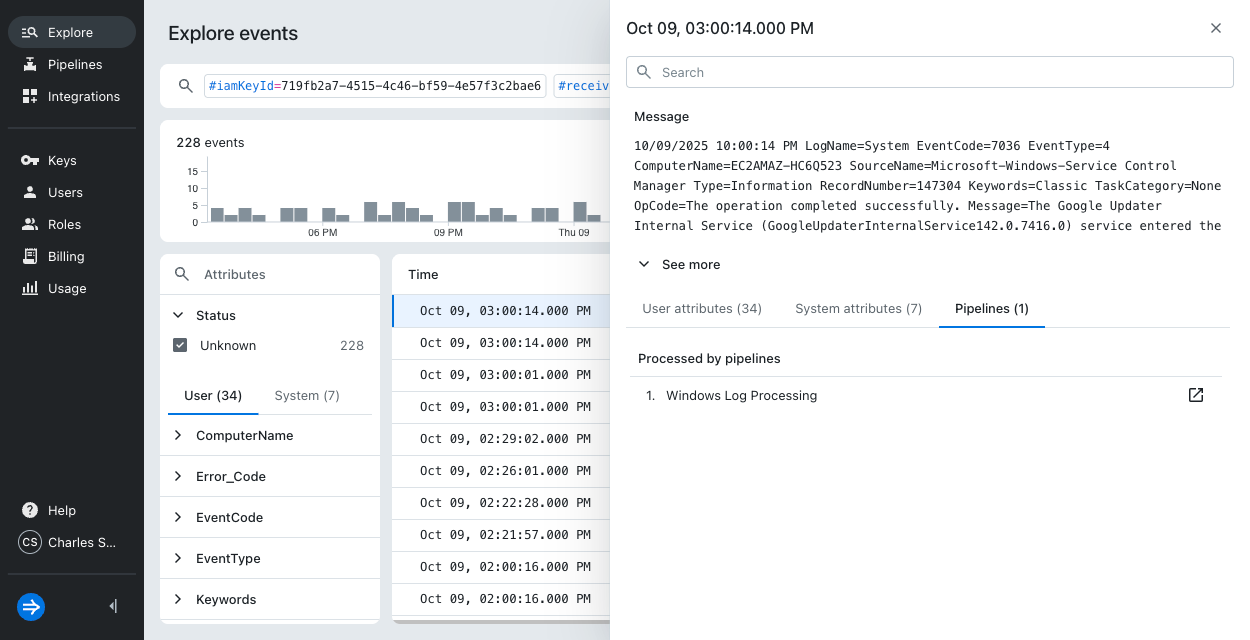
Learn more
Refer to the following topics for more information:
- Transform events with pipelines for an overview of pipelines in Lumi.
- Use predefined pipelines for details about predefined pipelines.