Map IdP groups to Polaris groups
If you enable Single sign-on (SSO) for Imply Polaris with Security Assertion Markup Language 2.0 (SAML) or OpenID Connect 1.0 (OIDC) identity protocols, you can set up group mapping from the identity provider (IdP) to Polaris. When you map IdP groups to Polaris groups, users who log in using the IdP are automatically provisioned to the corresponding groups in Polaris.
This topic explains how to map SAML and OIDC IdP groups to groups in Polaris.
Prerequisites
Before you map IdP groups to Polaris groups, make sure you have the following:
- An external IdP service that supports SAML or OIDC identity protocols.
- A Polaris account configured to use the SAML or OIDC IdP to authenticate. See Configure SSO for more information.
Configure group mapping
You can map IdP groups to groups in Polaris by passing group mapping values from the IdP to Polaris. Polaris supports one mapper per group. To map a single IdP group mapping value to multiple groups in Polaris, create multiple mappers.
Map a SAML IdP group
To map a SAML IdP group to a Polaris group, follow these steps:
- In the top right corner of the page, click the Administration gear icon.
- In the left sidebar, click Identity providers.
- Click Manage identity providers.
- Select the SAML IdP you want to configure group mapping for.
- Polaris displays the configuration page for your IdP. Click the Mappers tab.
- Click Add mapper to create a broker mapper. Broker mappers import SAML attributes into user attributes in Polaris.
- Enter information for the mapper:
- Name: Name of the mapper.
- Sync Mode Override: Specifies how to update user information at login. Choose from the following values:
- legacy: Keep the behavior before this option was introduced.
- import: Import user data from when the user was first created during the first login.
- force: Update user data at each login.
- inherit: Use the sync mode defined in the IdP.
- Mapper Type: Select
SAML Attribute to Group. - Attribute Name: Name of the attribute to search for in the SAML assertion. You can leave this field blank and specify Friendly Name only.
- Friendly Name: Friendly name of the attribute to search for in the SAML assertion. You can leave this field blank and specify Attribute Name only.
- Attribute Value: Attribute value as it appears in the SAML assertion.
- Group: Polaris group to assign the user to. Click Select Group to open the Group Selector dialog.
- Click Save.
The following screenshot shows a mapper called GroupMapper configured to pass the dataGovernance group mapping attribute from the SAML IdP to the Data Manager group in Polaris:
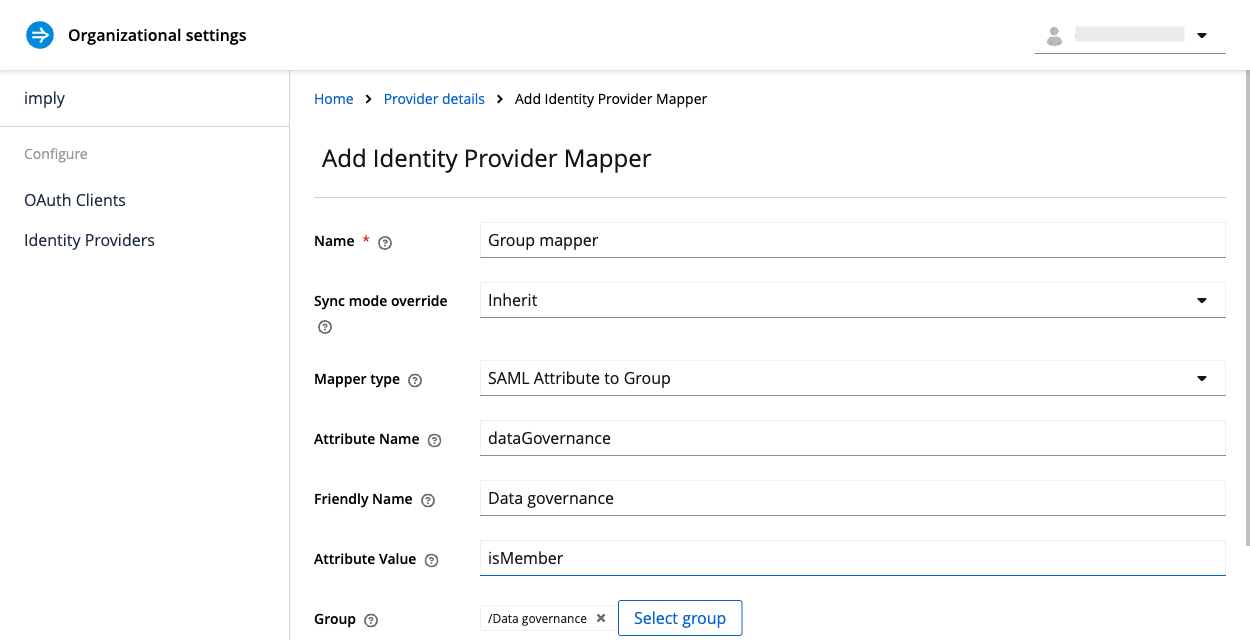
Map an OIDC IdP group
To map an OIDC IdP group to a Polaris group, follow these steps:
- Perform steps 1 through 4 of Map a SAML IdP group.
- On the Identity Providers page, select the OIDC IdP you want to configure group mapping for.
- Polaris displays the configuration page for your IdP. Click the Mappers tab.
- Click Create.
- Enter information for the mapper:
- Name: Name of the mapper.
- Sync Mode Override: Specifies how to update user information at login. Choose from the following values:
- legacy: Keep the behavior before this option was introduced.
- import: Import user data from when the user was first created during the first login.
- force: Update user data at each login.
- inherit: Use the sync mode defined in the IdP.
- Mapper Type: Select
Advanced Claim to Group. - Claims: Claim name and value to search for in the ID token of the IdP. You can reference nested claims using
.—for example,address.locality. To use a dot (.) literally, escape it with a backslash(\.). - Regex Claim Values: Specifies how to interpret claim values. If enabled, Polaris interprets claim values as regular expressions.
- Group: Polaris group to assign the user to if the claim is present. Click Select Group to open the Group Selector dialog.
- Click Save.
The following screenshot shows a mapper called Project Admin configured to map the manager claim name and the data-admin claim value from the OIDC IdP to the Project Admin group in Polaris:
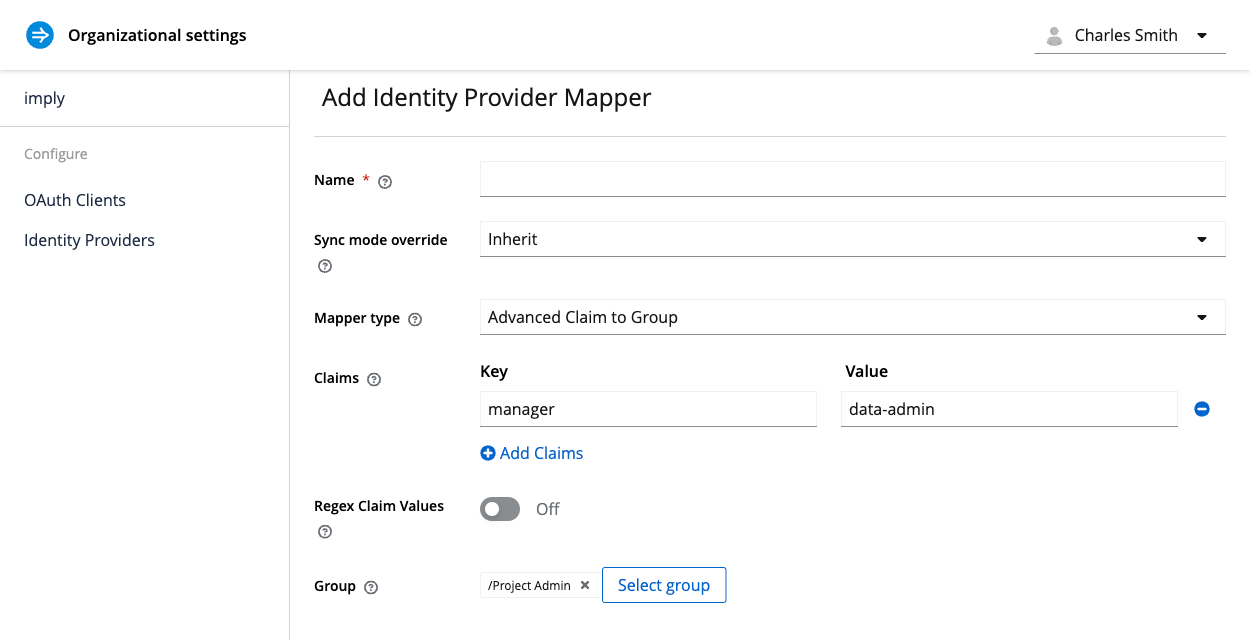
Learn more
See the following topics for more information:
- Enable SSO for configuring IdP-initiated SSO to authenticate to Polaris.
- SSO settings reference for SAML-specific configuration settings.