Okta OIDC integration
To enable Imply Hybrid (formerly Imply Cloud) Auth for your organization, contact your Imply account representative.
This topic describes how to configure Imply Hybrid to use Okta with OpenID Connect (OIDC) as an external identity provider.
Before you begin, make sure you are logged in as an administrator to both the Imply Hybrid and Okta consoles. Setting up an identity provider in the Imply Hybrid console requires User Manager role permissions.
Authentication
The following steps ensure that users can log in to Imply Hybrid with Okta:
- Set up an application in Okta for Imply Hybrid.
- Export the identity provider metadata document. This document includes the issuer's name, expiration, and keys to validate responses from the identity provider.
- Import the configuration into Imply Hybrid Auth.
Authorization
The following steps ensure that users can access certain assets in Imply Hybrid:
- Create groups in Okta, if not already present, to reflect usage in Imply Hybrid.
- Create composite roles in Imply Hybrid to map to the groups in Okta.
- Create mappers in Imply Hybrid to associate the groups to the composite roles.
Configure an Okta OIDC identity provider
The general flow for configuring an Okta OIDC identity provider is as follows:
- Add an identity provider
- Create an application in Okta
- Configure the OIDC settings
- Add user role mappings
Add an identity provider
- Log in to the Imply Hybrid User management console.
- Click Identity Providers from the left sidebar.
- Expand the Add provider section and click Open ID Connect v1.0.
- For Alias, enter a unique alias for the identity provider. Notice that the alias appears in the Redirect URI path. Imply Hybrid uses the alias to build the redirect URI and label the identity provider button on the login screen. Save the redirect URI value, since you will need it to create an application for Imply Hybrid in Okta.
Create an application in Okta
As an Okta administrator, log in to the Okta administration console and follow these steps to create an application integration for Imply Hybrid:
- In the Okta administration console, go to Applications > Applications.
- Click Create App Integration.
- For Sign-in method, select OIDC - OpenID Connect.
- Select Web for the type of application to integrate with Okta.
- Click Next.
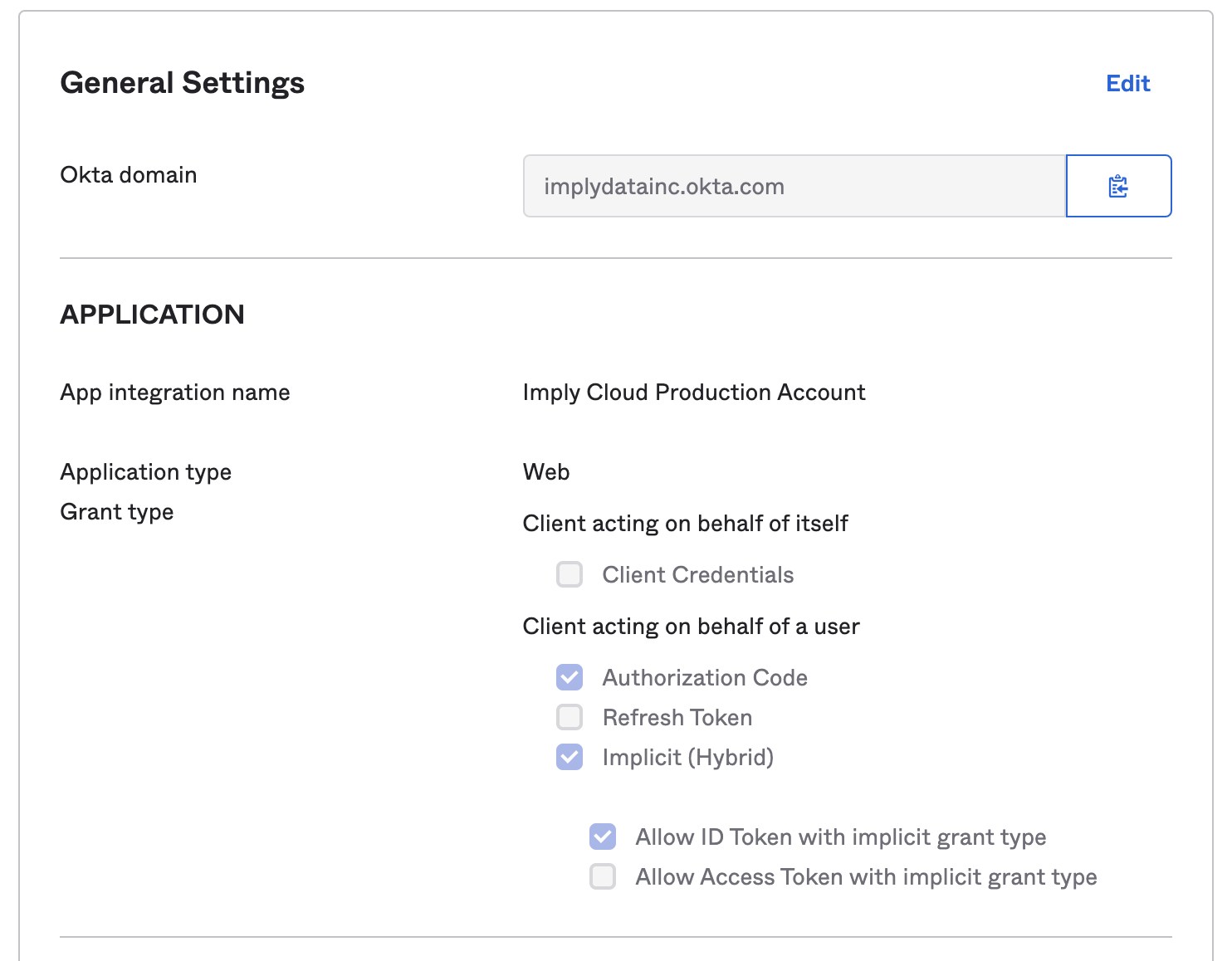
- In General Settings:
- Save the Okta domain value to use in the next section.
Note that you will also need the client ID and client secret, so keep both consoles open.
- Enable Authorization Code, Implicit (Hybrid), and Allow ID Token with implicit grant type options, as shown in the following screenshot:
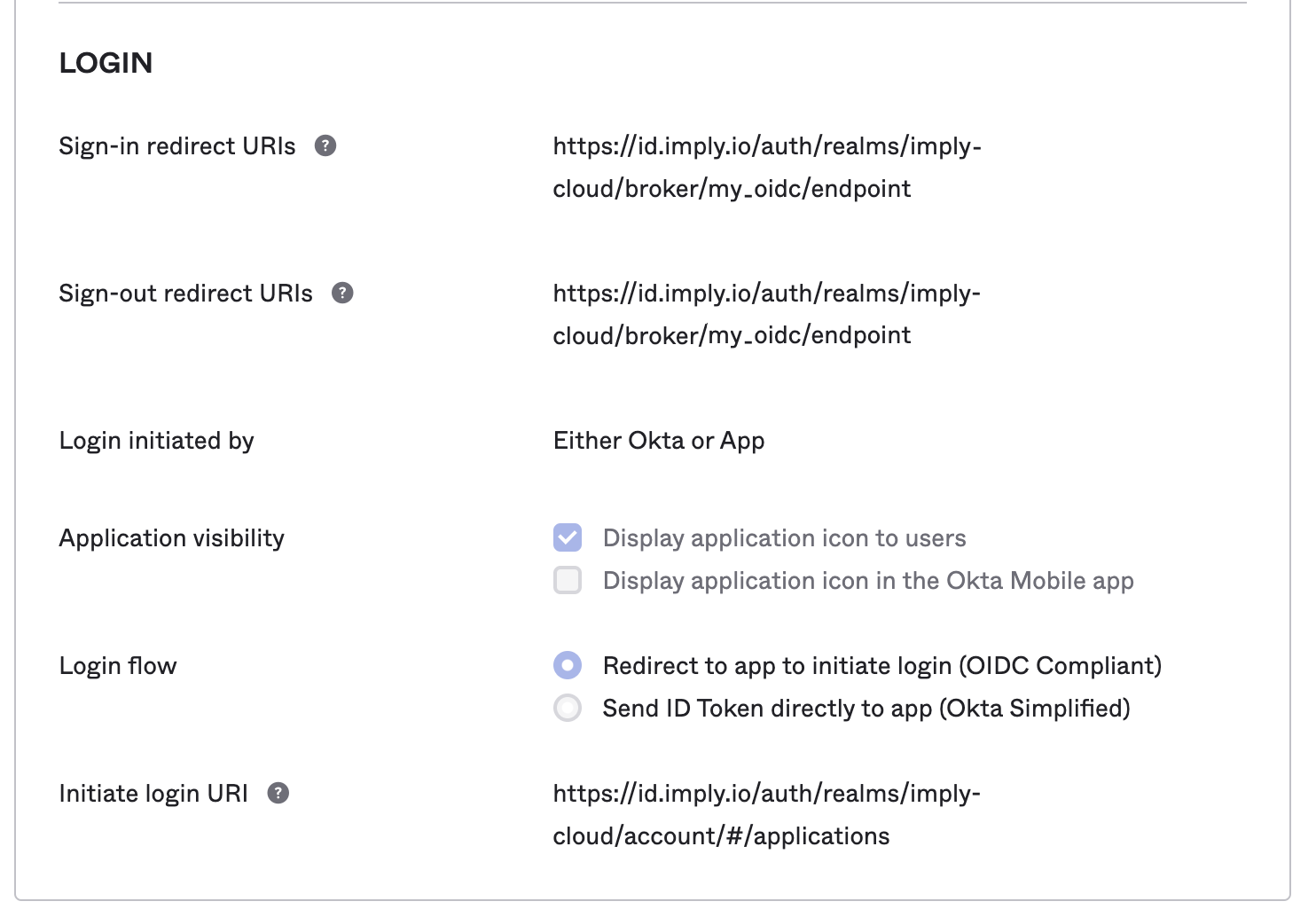
- Specify the redirect URI value you saved in Add an identity provider for Sign-in redirect URIs and, optionally, for Sign-out redirect URIs, as shown in the following screenshot:
- Save the Okta domain value to use in the next section.
- Complete the steps in the Okta application integration wizard, including assigning the app to users.
- Click Save.
Imply Hybrid Auth only supports service provider-initiated SSO.
Because of this, you cannot add Imply Hybrid as an app integration to your Okta Dashboard. Instead, create an Okta Bookmark App integration with the URL set to the login page https://ORGANIZATION_NAME.implycloud.com. Replace ORGANIZATION_NAME with the name of your organization.
For instructions on how to create a Bookmark App integration, refer to the official Okta documentation.
Configure the OIDC settings
Follow these steps to complete the setup of your identity provider in Imply Hybrid.
In the examples below, replace ORGANIZATION_NAME with the name of your organization.
-
In the Imply Hybrid User management console, click Identity Providers from the left sidebar.
-
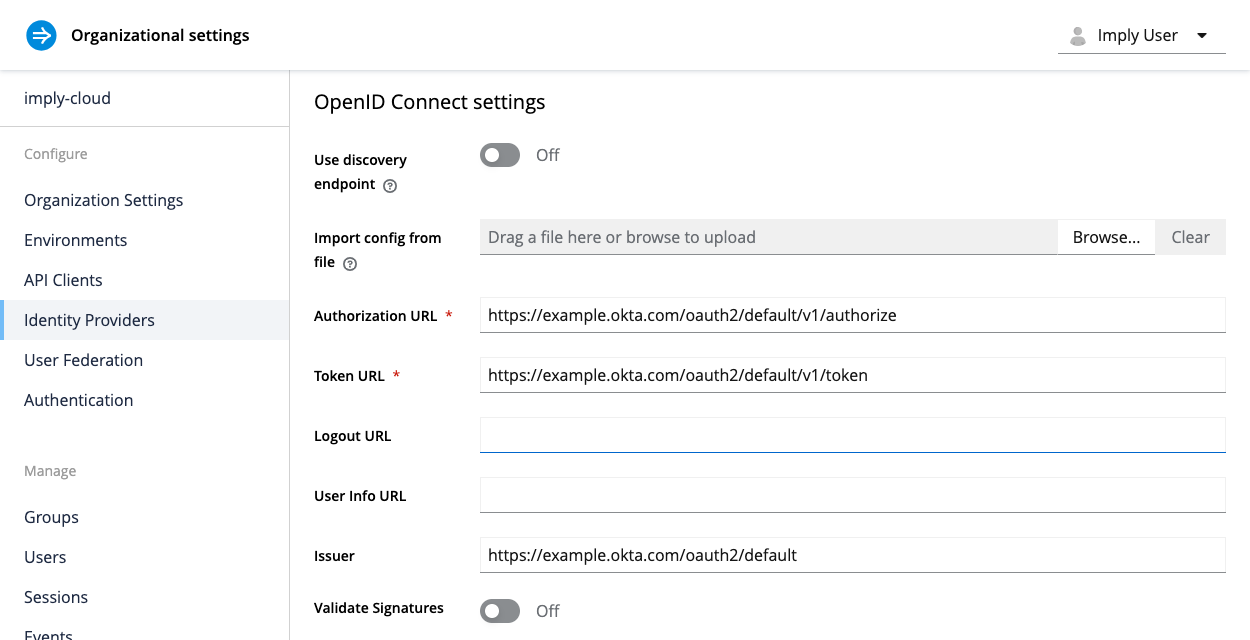
Complete the OpenID Connect settings section as follows:
- Use discovery endpoint: Disable this setting to prevent Imply Hybrid from loading the identity provider config from the discovery endpoint.
- Authorization URL: Enter
https://ORGANIZATION_NAME.okta.com/oauth2/default/v1/authorize. - Token URL: Enter
https://ORGANIZATION_NAME.okta.com/oauth2/default/v1/token. - Issuer: Enter
https://ORGANIZATION_NAME.okta.com/oauth2/default. - Client Authentication: Select Client secret sent as basic auth.
- Environment ID: Enter the Okta client ID value available from the Client Credentials section of the Okta UI.
- Client Secret: Enter the Okta client secret value available from the Client Credentials section of the Okta UI.
You can use default values for the rest of the settings. Your configuration should look similar to the following:
-
Click Add.
After you create the identity provider, you can choose the first login and post login flows. By default, the first login flow uses first broker login. See Common settings for more information.
You should now be able to access Imply Hybrid with an authenticated session. In most cases, you will want to map user attributes to roles in Imply Hybrid as described in the next section.
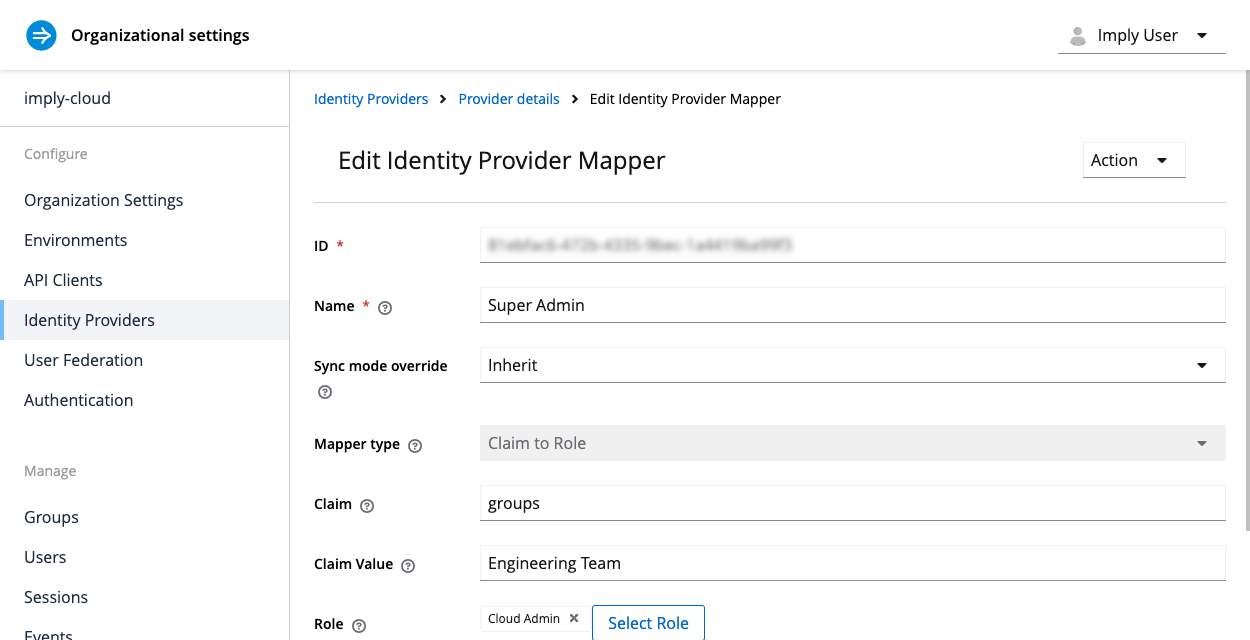
Add user role mappings
Mappers associate user properties from the identity provider to roles in Imply Hybrid. Before configuring mappers, determine which Imply Hybrid roles should be mapped to the Okta claims. You may need to create those properties for the purpose, if they don't already exist. To create claims in Okta, see Create Claims.
To add a mapper, follow these steps:
- In the Imply Hybrid User management console, click Identity Providers from the left sidebar.
- Click the name of the identity provider for which you want to configure mappers.
- Click the Mappers tab and then click Add mapper.
- Enter information for the mapper:
- Name: Name of the mapper.
- Sync Mode Override: Specifies how to update user information at login. Choose from the following values:
- Inherit: Use the sync mode defined in the identity provider. All other options override this sync mode.
- Import: Import user data from when the user was created during the first login.
- Legacy: Keep the behavior before this option was introduced.
- Force: Update user data at each login.
- Mapper type: Choose Claim to Role.
- Claim: Name of the claim as it appears in the OIDC token. For nested claims, use dot-delimited claim names, such as
admin.clusters. - Claim Value: Value of the claim to map to the Imply Hybrid role.
- Role: Imply Hybrid role to map the claim to. Click Select Role to browse roles. To reference an environment role, use the syntax
clientname.clientrole, for example,myclient.myrole.
- Click Save. Users can now log in to Imply Hybrid with authenticated Okta sessions.
The following screenshot shows a sample configuration that maps the groups claim to the Cloud Admin role in Imply Hybrid: