Secure connections to AWS
You can only use IAM role assumption when your Polaris cluster is hosted on AWS.
While S3 connections can also authenticate using AWS access keys, we recommend following security best practices to use IAM role assumption when possible.
To grant Imply Polaris access to your data in AWS, you establish a trust relationship between your AWS IAM role and the AWS IAM role of Imply. An IAM role is an identity with specific permissions that can be assumed by anyone who needs the role. The permissions assigned to the role are defined by IAM policies. For Imply to ingest your data, your AWS IAM role must have the following policies attached to the role:
- A trust policy that specifies which trusted account members are allowed to assume the role.
- A permissions policy that grants the user of the role the needed permissions to carry out the intended tasks on the resource.
The following diagram shows an example of the roles and policies involved in granting Polaris permission to read data from AWS Kinesis streams:
See the AWS documentation for more information about roles and cross-account access:
- IAM role management
- Role terms and concepts
- Policies and permissions in IAM
- Allow users from another account to access resources in your AWS account
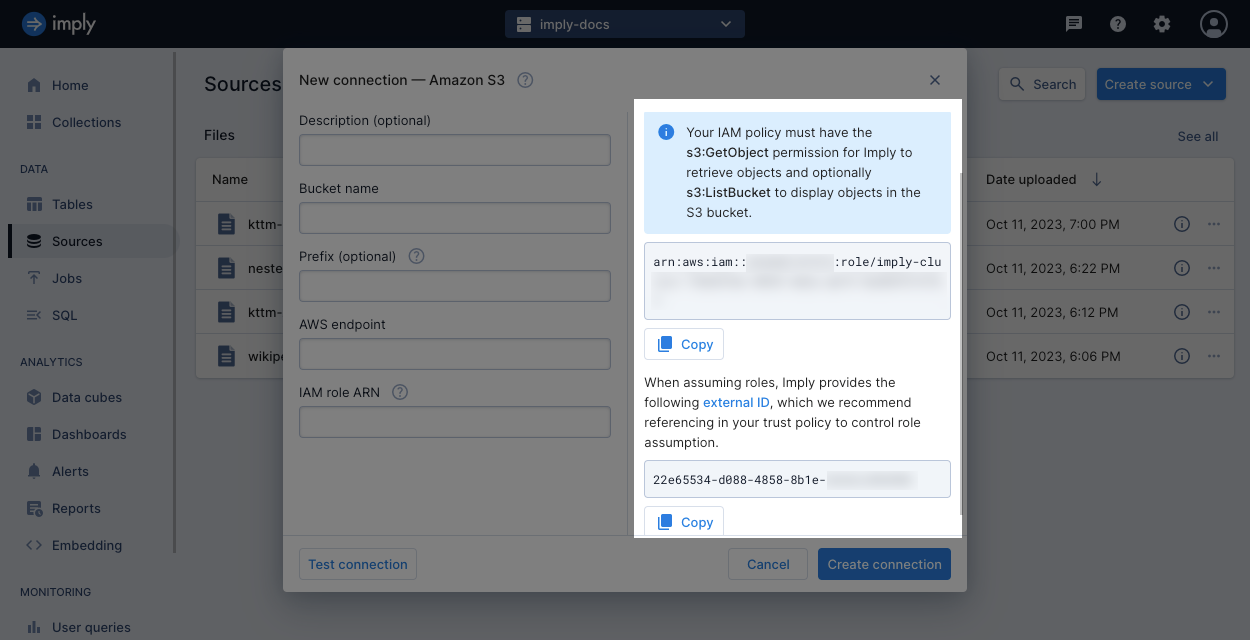
ARN for Polaris connection
When creating a connection to AWS resources, such as an S3 bucket or a Kinesis Data Stream, you provide
the ARN of your role
for Imply to assume to read and ingest the data.
For example, arn:aws:iam:::123456789012:role/demo-role.
Trust policy
To authorize access from Polaris to your AWS data, you must include the ARN of Imply's role to a
trust policy
attached to your AWS role.
List the ARN of Imply's role in the
Principal
field of the trust policy to allow Imply to assume your IAM role.
You can get the ARN of Imply's role using the API or when you create a connection in the UI.
For example:
External ID
Polaris also provides an external ID that you can use when granting Imply access to your AWS resources. We recommend adding the external ID in your trust policy to limit role assumption to your Polaris account's external ID.
When you include the external ID, this ensures that the role can only be assumed by another role when the role ARN is listed in the trust policy's Principal element and when the assume role request includes the same external ID.
For more information, see the AWS documentation on Using an external ID for third-party access.
Example trust policy
The following example shows a trust policy that authorizes Imply to assume your IAM role.
Replace the AWS and sts:ExternalId values with the appropriate ARN and external ID for your project.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::987654321098:role/imply-cluster-3b538a72-844f-4a09-883d-xxxxxxxxxxxx"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {"sts:ExternalId": "3b0x43c2-7fx0-4x23-a4fx-9256ce8205xx"}
}
}
]
}
For more information on trust policies on an IAM role, refer to the AWS documentation.
Permissions policy
In a permissions policy that you attach to your IAM role, you list the resources that the role can access and set the level of access by listing the allowable actions. Each AWS service has its own actions, resources, and condition context keys for use in IAM policies. The reference information for Polaris connections lists the required permissions to access each AWS resource.
For more information on creating a permissions policy, see the AWS documentation on Actions, resources, and condition keys for AWS services.
Learn more
See the following topics for more information:
