Audit logs
Audit logs capture authentication and administrative events for your organization in Imply Polaris. You can use audit logs to detect anomalous activities and investigate potential misuse of privileges or security incidents.
This topic explains how to view audit logs in the Polaris UI. To retrieve audit logs through the Polaris API, see the Audit API documentation.
Prerequisites
Users with the AccessAuditLogs permission and members of the Organization Admin group can view audit logs in Polaris. For information on permissions, see Permissions reference.
View audit logs
Audit logs provide contextual information based on the category and type of action.
Polaris retains audit logs for a minimum of 31 days.
You cannot modify or delete audit logs.
To view audit logs in the Polaris UI, click the gear icon in the top right corner to open the Administration console. Click Audit logs in the left navigation pane to access the main Audit logs page:
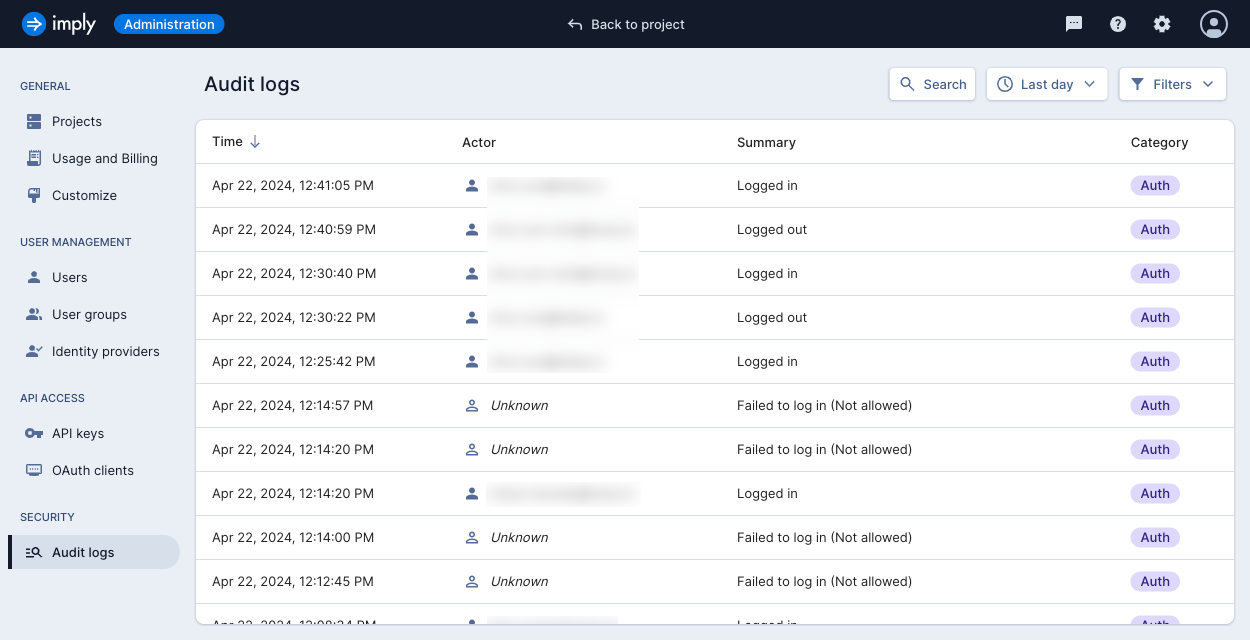
Each logged event contains the following fields:
- Time: date and time the event occurred
- Actor: user who triggered the event
- Summary: description of the event
- Category: category of the event
Logged events may include additional fields based on their category:
- IP address: IP address of the user who triggered the event
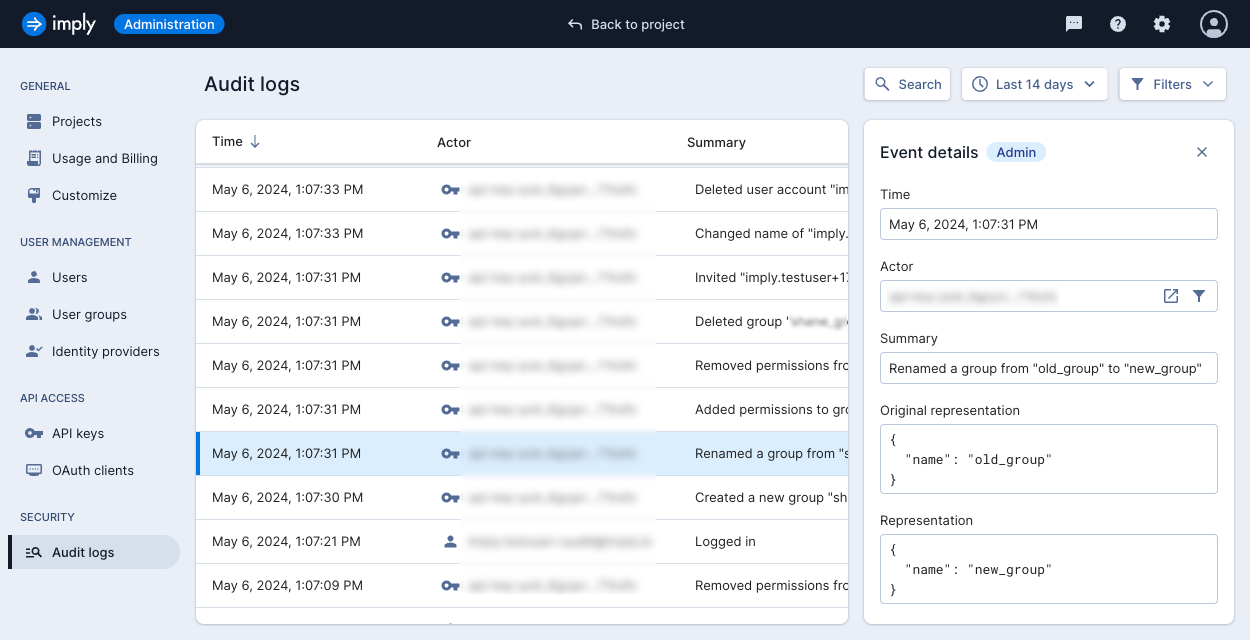
- Original representation: state of the resource before the event occurred
- Representation: state of the resource after the event
Click on a log to view its details:
Logged events
This section describes the events captured by Polaris, grouped by event category.
Authentication events
The Auth category encompasses user authentication events.
Polaris provides logs for the following types of user authentication events:
- Successful user login
- Failed user login
- Logout
- Password reset requested
- Password updated
- User impersonated
- User invite accepted
Administrative events
The Admin category encompasses administrative events.
The following table shows the types of administrative events recorded by Polaris:
| User events | Group events | API key events |
|---|---|---|
| User created | Group created | API key created |
| User updated | Group updated | API key updated |
| User deleted | Group deleted | API key deleted |
| User name changed | Group name changed | API key name updated |
| User enabled | Group permissions added | API key permissions added |
| User disabled | Group permissions removed | API key permissions removed |
| User invite sent | Group scope all projects | API key scope all projects |
| User password reset | Group scope specific projects | API key scope specific projects |
| User groups added | Group member added | API key description updated |
| User groups removed | Group member removed |
Search audit logs
You can use the search bar to narrow down events according to your specified criteria.
Filter by date range
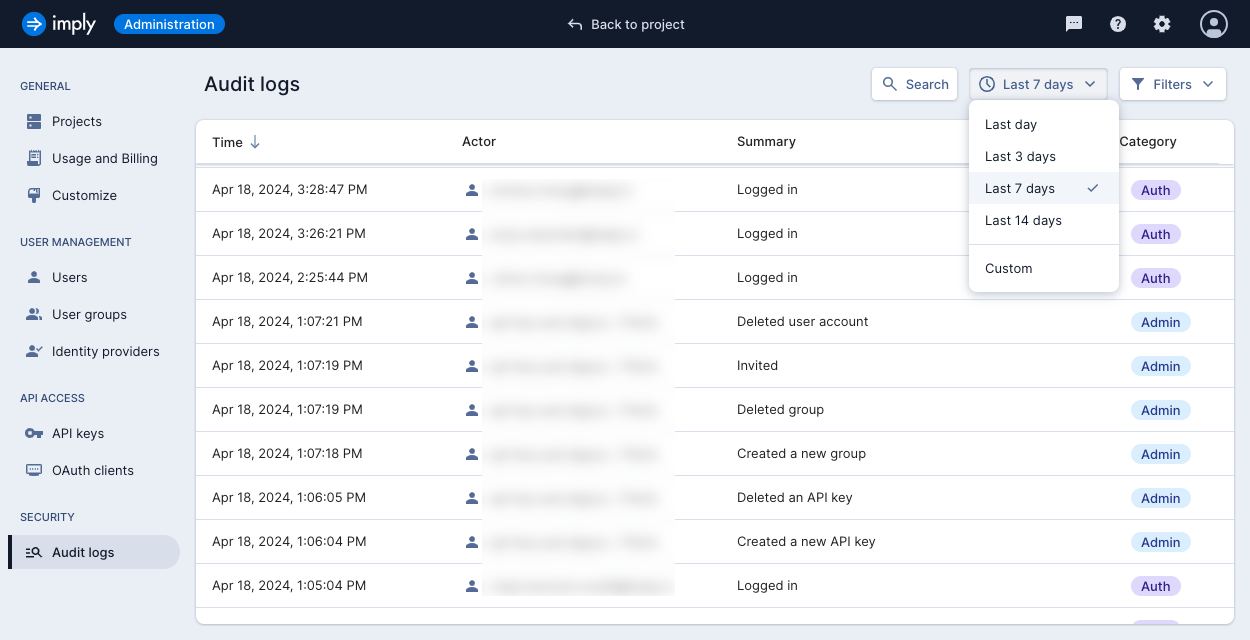
To find events within a date range, click the date drop-down and select one of the available options:
- Last day
- Last 3 days
- Last 7 days
- Last 14 days
- Custom
To use a custom range, select Custom from the date drop-down and enter the start and end dates.
Other filters
You can apply additional filters to refine your results. Click the Filters drop-down to view available options. You can filter by user email, event category, or IP address.